CNC Router Network Security (Fanuc)
I recently gave a talk at the Queen City Skiddies (QCS) meetup in Charlotte, NC. I feel that it was a well-received presentation and so I wanted to put the information out there for those who were not able to attend. As well as covering the material in the presentation, I wanted to go a bit further.
CNCs are becoming smarter every day. We are adding new hardware and software to make the CNC easier and more user-friendly. This does not come without some downsides, and it is some of those downsides that I wanted to cover.
The news headlines make it apparent that computer security is under attack. From Sony to critical infrastructure, no entity is immune from the relentless masses of hackers looking to steal your information.
But what happens when the information the hackers are after is your intellectual property? What if they obtain it is through the very machinery used to produce your end products?
Security Risks

A CNC can be an integral part of your company’s operations. Without your CNC you may be spending money to have a third-party fabricate your parts. You may even have to use a more manual method of producing your parts. But, when was the last time you stopped to consider the security of that CNC on your network?
What if a hacker was able to steal the design for the parts you are producing? Would that have an impact on your competitive advantage? What about if those programs were erased? How much would it cost to recreate those programs?
Those are not the only threats! For example, what if a hacker had the ability to remotely control your CNC machine? Or, what if they could cause damage to it or to the operator who runs the machine?
These are real threats and something that you should be concerned about.
When we put a CNC on our network, the intent is usually to ease the process of monitoring the CNC and transferring jobs. While a small shop may be able to bring each job out to the machine, it is not always feasible. For example, a large organization with split offices and manufacturing facilities would find this very cumbersome.
However, when we put a third-party piece of machinery on our network, we need to understand the risks that come along with it. We need to think about how that monitoring software or job transfer is taking place, and how it might be exploited by an opportunistic hacker.
This is the Way!

The communication between a CNC and other devices on the network is often facilitated by an Application Programming Interface or API. Each control manufacturer will supply its own API that allows outside applications to interface with the machinery.
While we are going to focus primarily on the API supplied by Fanuc, this should also be relevant to other CNC control manufacturers. You should contact your machine manufacturer if you are not sure whether something is applicable to your CNC.
An API is a mechanism that allows the software to interact with the machine. In the right circumstance, this API can be leveraged for malicious purposes. Let’s take a look at what we can do with the Fanuc API, called Focas.
Read, Write, and Be Merry
One of the things we can do is read information from the CNC using the Focas API. For example, I could read the active program. Another thing I could do is look at the positions of each of the axes.
While reading information from the CNC may normally not be a threat, there are ways an attacker may misuse the ability. For example, if you are a military contractor, the parts you cut may be classified. There may be any number of reasons you may not want someone to have access to your programs.
With the ability to read from the CNC, an attacker could download all of the programs you spent thousands of dollars developing.
As well as the ability to read, attackers with network access will have the ability to write information to the CNC. An attacker could potentially alter your programs, change the machine configuration, or even make the machine move.
What if an attacker used the API to send a command to the CNC to start the spindle and plunged it into the table? This could cause severe damage to the machine, or even an operator if they are in close proximity.
For more information on the Fanuc Focas API and what it can do, be sure to check out my 3-part series on Fanuc Focas programming with C#!
The main problem with the abuse of CNC APIs is that they often do not require any form of authentication. What this means is that so long as I have access to a computer on your network, I can create a program to interact with the CNC. The CNC does not check to see who I am when I send it a command, it just executes it.
Is Your CNC Vulnerable?

So how would you know if your machine is vulnerable? Well, in order to make calls to the machine, you need access to the CNC control. The CNC control is usually different than the Human Machine Interface (HMI), which is what the operator uses to run the machine.
The control will usually be a small box in the electrical cabinet of the machine that acts as the brain. The HMI, axis drives, and input/output interface will all be connected to the control and the control will take care of processing all the information.
If the control is not directly accessible by the network, the attack vector is much smaller, but not completely eliminated.
To see if the control is accessible via the network, you may need to rely on the vendor-supplied schematics. If there is an Ethernet cable coming out of the CNC control, you may be able to trace it to see if it is connected to an internal switch and if that switch is connected to your network.
Find a Machine!
Penetration testers might take a different route. By sniffing network traffic with your favorite application, you can analyze the packets to see if they contain clues that a CNC controller is on the network. Let’s take a look at an example.
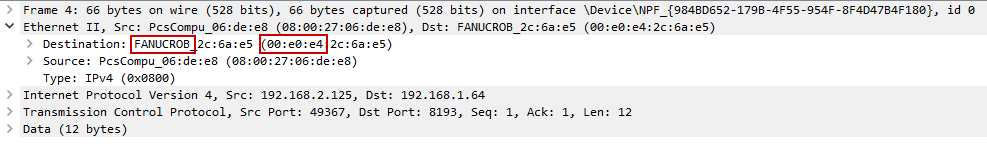
This is the result of a packet capture I took. I ran a sample application that connected to a known CNC controller on the network. In this instance, we can see that the MAC address indicates the destination is a Fanuc device.
While Fanuc may use their own devices, this may not be the case for other CNC manufacturers. As of this writing, I have not been able to find any information in the packet capture data that would help indicate the Focas API is being used. If you have any information regarding this, please feel free to reach out or comment below!
Unsafe CNC Networking
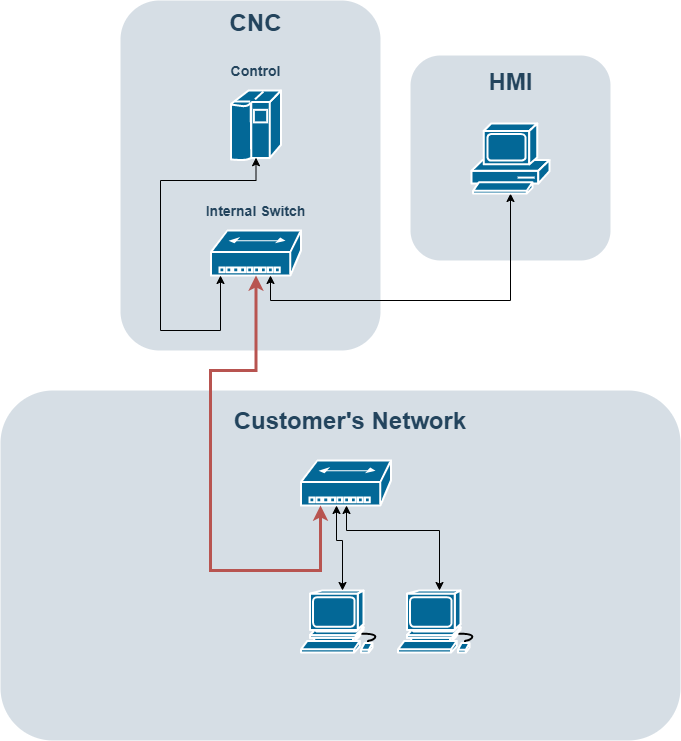
The image above shows how a CNC in your plant can be networked in an unsafe manner. As you can see, the facility has the CNC on its network. The facility network switch is run directly to the internal switch of the CNC machine.
The problem with this setup isn’t that the machine is on the facility’s network, but that the CNC control is also connected to the switch. In order for the HMI to communicate with the control, they need to be connected.
An attacker now has direct access to make API calls to the CNC control. This is an all too common setup, especially in smaller shops where there is no dedicated IT staff.
Let’s take a look at how we can improve the network setup to help prevent direct access to the CNC control.
Safe(er) CNC Networking
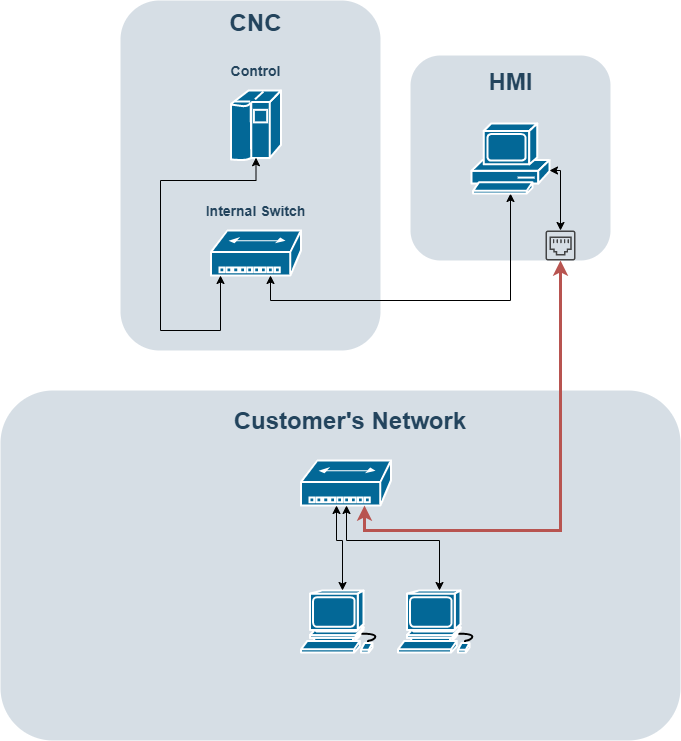
The above image shows how we can make changes that help improve the security of our CNC. The HMI in the previous example shows the HMI connected to the internal switch. In this example, we have an HMI that has two network adapters. This is common on newer Fanuc machines.
We have created a dedicated connection from the HMI to the facility’s network. This method prevents direct access to the CNC control. Now, if an attacker wants to get to our CNC machine, they will need to compromise the HMI. While this is not impossible, it greatly improves security.
Other Methods
What happens if the CNC doesn’t have an extra Ethernet port on the HMI? You will find this is the case in older Fanuc machines and possibly other CNC manufacturers. But all is not lost!
One other method is to create a dedicated network for your CNC machines. Using a dedicated network and routing between your company’s network and the CNC network will add another layer of security. This prevents someone from accessing your internal network and having quick access.
Extreme Method
The most extreme, but also most secure option is to completely remove the CNC from the network altogether. This is probably not a viable option for a large portion of the CNC-owning population, but it will improve security! In this case you will need to manually transfer jobs to the CNC using a USB.
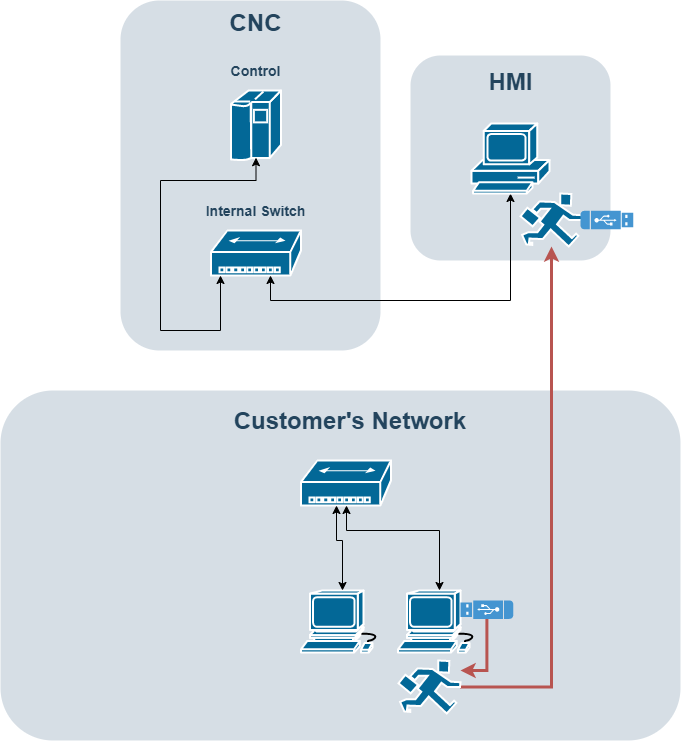
Conclusion
CNC security is one of those things that people don’t tend to think about until it is too late. With the increasing number of cyber attacks, it is only a matter of time until CNC’s find themselves the target of threat actors looking to make a buck. For those who rely on CNCs to keep their businesses running, the time is now to start taking the threat seriously.
Questions and comments are welcome. Let’s get the conversation started!
3 thoughts on “CNC Router Network Security (Fanuc)”
Leave a Reply
You must be logged in to post a comment.
Great work Matthew. Lots of real information in this presentation.
Thank you! I tried to make it easy for everyone to understand and still get the information through. Glad you enjoyed it.
Fanuc has published some known vulnerabilities regarding their ethernet implementation:
A-42146-00243EN